DeepGuard: A Hybrid RF-CNN-GRU Framework for Adaptive Real-Time Zero-Day Network Intrusion Detection
DOI:
https://doi.org/10.26438/ijsrcse.v13i3.687Keywords:
Network Intrusion Detection, Artificial Intelligence, Anomaly detection, Random Forest, Convolutional Neural Network, Gated Recurrent UnitAbstract
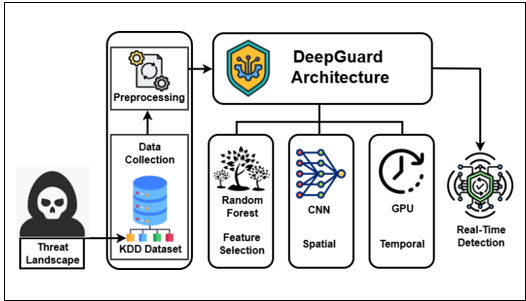
Due to the dynamic and ever-increasing nature of cyber threats, the traditional network intrusion detection systems (NIDS) are not sufficient and are slow to respond to the adapting of new threats since they utilize rigid rules and signature-based detection techniques. This research study aims to design an intelligent adaptive intrusion detection system capable of precise and prompt detection of both established and latent threats to the network. Achieving optimal results from feature extraction, spatial pattern recognition, and temporal sequence learning requires a hybrid model that synergistically combines Random Forest, Convolutional Neural Network, and Gated Recurrent Unit (GRU). The model was built in Python using TensorFlow and Scikit-learn, training and testing it with the KDD Cup 1999 dataset. The experimental results indicated that the proposed model outperformed existing models, achieving an accuracy of 99.23%. This finding confirms the effectiveness of integrating multiple deep learning models. The research data illustrates how the models effectively resolve a basic cybersecurity challenge during active performance.
References
M. Zipperle, F. Gottwalt, E. Chang, T. Dillon, “Provenance-based Intrusion Detection Systems: A Survey,” ACM Computing Surveys, Vol.55, Issue.7, pp.135:1–135:36, 2022.
O. H. Abdulganiyu, T. Ait Tchakoucht, Y. K. Saheed, “A Systematic Literature Review for Network Intrusion Detection System (IDS),” International Journal of Information Security, Vol.22, Issue.5, pp.1125–1162, 2023.
S. Neupane et al., “Explainable Intrusion Detection Systems (X-IDS): A Survey of Current Methods, Challenges, and Opportunities,” IEEE Access, Vol.10, pp.112392–112415, 2022.
E. E. Abdallah, W. Eleisah, A. F. Otoom, “Intrusion Detection Systems Using Supervised Machine Learning Techniques: A Survey,” Procedia Computer Science, Vol.201, pp.205–212, 2022.
P. Vanin et al., “A Study of Network Intrusion Detection Systems Using Artificial Intelligence/Machine Learning,” Applied Sciences, Vol.12, Issue.22, pp.1–17, 2022.
B. Susilo, A. Muis, R. F. Sari, “Intelligent Intrusion Detection System Against Various Attacks Based on a Hybrid Deep Learning Algorithm,” Sensors, Vol.25, Issue.2, pp.1–20, 2025.
M. Sajid et al., “Enhancing Intrusion Detection: A Hybrid Machine and Deep Learning Approach,” Journal of Cloud Computing, Vol.13, Issue.1, pp.1–20, 2024.
V. G. da Silva Ruffo, D. M. B. Lent, M. Komarchesqui, V. F. Schiavon, M. V. O. de Assis, L. F. Carvalho, M. L. Proença, “Anomaly and Intrusion Detection Using Deep Learning for Software-Defined Networks: A Survey,” Expert Systems with Applications, Vol.256, pp.1–27, 2024.
S. Neupane et al., “Explainable Intrusion Detection Systems (X-IDS): A Survey of Current Methods, Challenges, and Opportunities,” arXiv preprint, arXiv:2207.06236, pp.1–30, 2022.
K. A. Shukla, S. Ahamad, G. N. Rao, A. J. Al-Asadi, A. Gupta, M. Kumbhkar, “Artificial Intelligence Assisted IoT Data Intrusion Detection,” International Conference on Computing and Communications Technologies (ICCCT), Chennai, India, pp.330–335, 2021.
G. Narayanan, M. S. Ali, S. Ahamad, “Cyber Secure Consensus of Discrete-Time Fractional-Order Multi-Agent Systems with Distributed Delayed Control Against Attacks,” IEEE International Conference on Systems, Man, and Cybernetics (SMC), Melbourne, Australia, pp.2191–2196, 2021.
K. A. Kumari, S. Ahamad, T. Patil, K. Sardana, E. Muniyandy, D. Pilli, “Neural Network Pruning Techniques for Efficient Model Compression,” International Journal of Intelligent Systems and Applications in Engineering, Vol.12, Issue.15s, pp.565–572, 2024.
T. Anitha, K. N. Mishra, V. Talukdar, K. S. Priya, S. Ahamad, A. Gupta, “Securing IoT Networks: Leveraging Big Data for Enhanced Resilience,” International Conference on Computing Communication and Networking Technologies (ICCCNT), Kamand, India, pp.1–6, 2024.
S. Ahamad, B. Rao, K. Srikanth, V. Gopal, P. Mehra, M. Alazzam, “Machine Learning Approach to Enhance Performance of Suspicious Activity Detection System,” AIP Conference Proceedings, Vol.090005, pp.1–6, 2023.
S. J, K. Kanagasabapathi, K. Mahajan, S. Ahamad, E. Soumya, S. Barthwal, “AI-Enhanced Multi-Cloud Security Management: Ensuring Robust Cybersecurity in Hybrid Cloud Environments,” International Conference on Innovative Computing, Intelligent Communication and Smart Electrical Systems (ICSES), Chennai, India, pp.1–6, 2023.
“KDD Cup 1999 Dataset,” UCI Knowledge Discovery in Databases Archive, University of California, Irvine, 1999. Accessed: May 8, 2025.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Asfa Praveen

This work is licensed under a Creative Commons Attribution 4.0 International License.
Authors contributing to this journal agree to publish their articles under the Creative Commons Attribution 4.0 International License, allowing third parties to share their work (copy, distribute, transmit) and to adapt it, under the condition that the authors are given credit and that in the event of reuse or distribution, the terms of this license are made clear.






